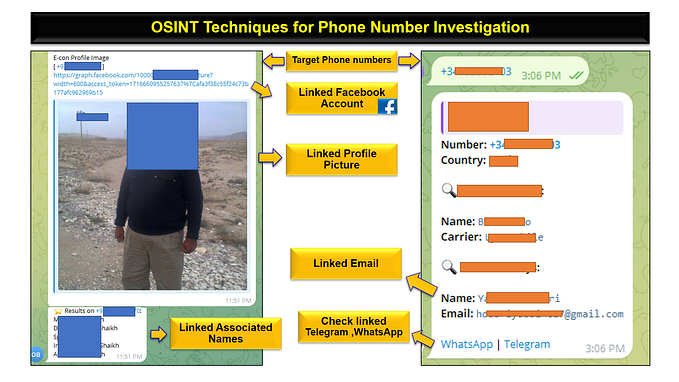
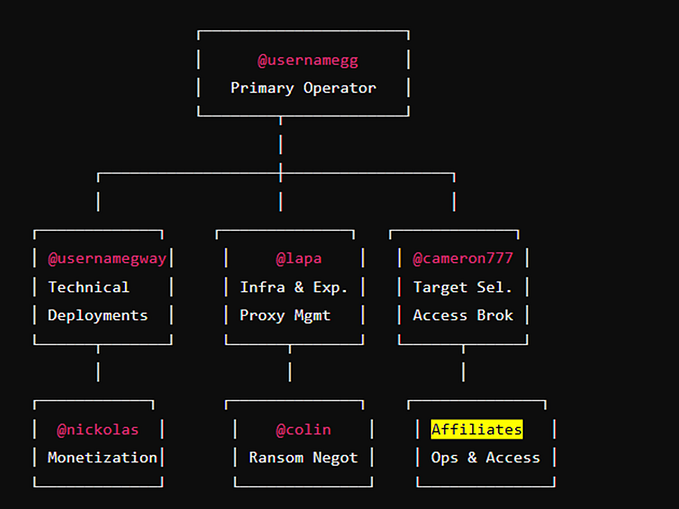
Forced Information Gathering…
Ethical but Offensive — OSINT

Hey, fellow earthling!
How’s it going?
- I hope you had a good time & thanks for popping by.
Today, we will examine a few offensive tools, some even unmentionable. Check the images or read my further ninja writing. You will understand …;)…. As we all know, OSINT or Open Source Intelligence should mean ONLY OPEN SOURCE, right? Yes, but there comes the twist.
- When investigating, pen-testing, studying, or working, we may incur unwanted outcomes; indeed, we should always be able to tackle the issues calmly along with the right tools & mindset.
Unlike conventional OSINT, Offensive OSINT uses tools & techniques similar to malware or Social Engineering to gather more aggressively information. The line between OSINT & Hacking is cloudy, yet it needs to be officially defined.
It’s all about the professionals behind the scenes & their background, experience, dedication, & creative mindset, which make a significant difference in real-life scenarios.
As we delve into information gathering & cybersecurity, it’s essential to understand the distinction between Open Source Intelligence (OSINT) & Hacking. While both involve gathering information, the legal & personal implications differ. OSINT is a legal & ethical practice of collecting information from publicly available sources, whereas Hacking is illegal & can lead to serious legal consequences. In addition to the legal implications, Hacking can have serious personal consequences, such as damage to reputation or trust. So, it’s essential always to approach information gathering with the right mindset & tools.
Open-source intelligence (OSINT) gathers information from publicly available sources, such as social media, search engines, news articles or grey literature & more. The goal is to collect intelligence legally and ethically without infringing on anyone’s privacy or breaking laws. On the other hand, offensive OSINT involves using techniques similar to those used in Hacking, including malware, to gather more information. Security professionals typically use it to identify system vulnerabilities or gather intelligence on potential threats. Indeed, Pentesting, is not Hacking.
-One of the main differences between OSINT and Offensive OSINT is the legal and ethical implications. While OSINT is legal and moral, Offensive OSINT can be illegal and unethical if not carried out responsibly. Gathering information with the right mindset and tools is essential to avoid legal or ethical issues.
Here are a few real-life examples:
- OSINT:
A company conducting background checks on a potential employee by searching for their publicly available information online.
- Offensive OSINT:
A security professional using malware to gather information on a potential company network threat.
- OSINT:
A journalist researching a story by searching for information on social media and news articles.
- Offensive OSINT:
A hacker or Detective using malware to gather personal information from targets.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — -
Before digging in, please remember that this is only for Educational Purposes, and you are the only one in charge of your actions, OK?
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
Further this we can start…
Seeker
The idea behind Seeker is relatively straightforward. In the same way we create phishing pages to obtain login credentials, why not set up a fake website that requests your location, as many popular location-based websites do? Seeker creates a phoney webpage that prompts the user for location permission. If the target consents, we can retrieve:
- Longitude
- Latitude
- Accuracy
- Altitude
- Direction
- Speed
- Unique ID using Canvas Fingerprinting
- Device Model
- Operating System
- Platform
- Number of CPU Cores — Approximate Results
- Amount of RAM — Approximate Results
- Screen Resolution
- GPU information
- Browser Name and Version
- Public IP Address
- Local IP Address
- Local Port
After receiving the above information, an Automatic IP Address Reconnaissance is conducted.
The above is on their page, which worked for me when I tested it. Even if I could not download all the specs, I can give a thumbs up to it and their project. The same tool is often used for hacking/information gathering or as a geo-location tool, but it is often used for offensive OSINT or malicious actors.
CiLocks
This is another highly effective hacking tool that can deliver robust results when investigating or pen testing. It can be used with MSF, making it a strong, flexible, and multi-faceted tool that can penetrate the core when actively gathering information from the target. To know more about MSF, check out the information below. You can also find a copy and paste of their latest update to better understand the tool’s power.
Update Available V2.1 🚀
- Added New Tools
- Root Android {Supersu} Not Support All OS Version
- Jump To Adb Toolkit
- Shell
- ScreenShot
- Copy All Camera Photo
- Copy All WhatsApp Folder
- Copy All Data Storage
- Manual Copy {Costum}
- Backup Data
- Restore Data
- Permissions Reset
- Reboot
- Remove Lockscreen {Root}
- Jump To Metasploit
- Install Application
- Create Payload Backdoor {Msfvenom} Singed
- Run Metasploit
- Inject Payload In Original Application
- Phone Info
- Control Android {Scrcpy}
- Brute Pin 4 Digit
- Brute Pin 6 Digit
- Brute LockScreen Using Wordlist
- Bypass LockScreen {Antiguard} Not Support All OS Version
- Reset Data
- IP Logger (Track IP Location and Information)
- SpyCam (Take webcam shots from the target just sending a malicious link)
- IOS Payload
- FireStore Vulnerability
Credits: https://github.com/tegal1337/CiLocks
I tested it personally, and yes, it works totally as advertised. Even if it is not new user-friendly, it can be highly effective in the field. Remember, this is Offensive OSINT, and this is a Hacking Tool.
Be cautious.
XTEAM
I have yet to try it, but I’ve come across a tool that seems invasive. It has been Forked 63 times and Starred 638 times, indicating that it works well. Furthermore, several tutorials, reviews, and forums discuss it. According to the advertisement, it is an ideal tool for Xteam All-in-One, offering Instagram, Android, phishing sites, and Wi-Fi hacking tools.
Below is their Github README paste.
Features:
- Insta information gathering
- Crack android lockscreen interfaces
- Phishing Hacks
- Wireless attacks added
- Update script
- Remove script
- more coming…
Requirements
- Data connection
- No Root
Available On
- Termux
- Kali Linux
Test On:
- Termux
- Debian
INSTALLATION [Termux]
- apt update
- apt upgrade
- pkg install python
- pkg install python2
- pkg install git
- git clone https://github.com/xploitstech/Xteam
- ls
- cd Xteam
- pip3 install -r requirements.txt
- chmod +x *
- bash setup.sh
- bash Xteam.sh
INSTALLATION [Kali Linux]
- sudo apt install python
- sudo apt install python2
- sudo apt install git
- git clone https://github.com/xploitstech/Xteam
- ls
- cd Xteam
- pip3 install -r requirements.txt
- chmod +x *
- sudo bash Xteam.sh
Warning:
This tool is only for educational purposes. If you use this tool for other purposes except education, we will not be responsible in such cases.
R4ven
This tool is a real eye-opener for those curious about how a malicious website can gather sensitive information about you and your devices. It allows you to simulate a fake website that displays a legitimate website within an iframe. The exciting part is that if the target allows it, this tool can fetch the person’s GPS location (latitude and longitude), capture multiple pictures of them, and obtain their IP address and device information. By using this tool, you can easily understand the risks associated with clicking on random links or granting permissions like location to suspicious websites. It’s a reminder that even a seemingly innocent website can be used as a tool for cybercriminals to collect sensitive data.
So, before you click on any link or grant permission to any website, remember to exercise caution and think twice about the risks involved. Use this tool to learn more about protecting yourself and your devices from online threats.
Here are some of their README.md file below:
This tool is a Proof of Concept and is for Educational Purposes Only.
Key Features:
- IP address and geographic location tracking
- Collection of device system information
- Capturing images from the device’s camera
- Integration with Discord for data presentation
- User interaction for location permission
- Display of a website through an embedded iframe
- Regular interval-based data collection
- Access to and upload webcam images
- Formatting and presentation of data in Discord messages
- Links to Google Maps and Google Earth based on location
- Error handling for denied location permission
- User feedback and error messages
On the link click
+ It will automatically fetch the IP address and device information
! If location permission is allowed, it will fetch the exact location of the target.
! If camera permission is allowed, it will capture non-stop from the front camera.
Limitation
- Make sure you port forward else it will not work on the smartphone’s browser
# Most browsers auto block extra permissions for ip based URL. so port forward!!
- It will not work on laptops or phones that have no GPS or no Camera,
# browsers that block javascript,
# or if the target is mocking the GPS location.
# or if a target is using VPN or spoofing IP
- Some browsers auto block location permission like(Brave, Safari etc)
+ Best work with Chrome browser
+ Location accuracy will be more accurate if you use this on a smartphone.
IP location VS. GPS location
- Geographic location based on IP address is NOT accurate,
# Does not provide the location of the target.
# Instead, it provides the approximate location of the ISP (Internet service provider)
+ GPS fetch almost exact location because it uses longitude and latitude coordinates.
@@ Once location permission is granted @@
# Accurate location information is received to within 20 to 30 meters of the user’s location.
# (it’s almost the exact location)
Here again, this is another highly effective tool that requires medium/high experience in computer languages, OS, CLI, etcetera. It will surely be overwhelming for new beginners but easier for students and professionals.
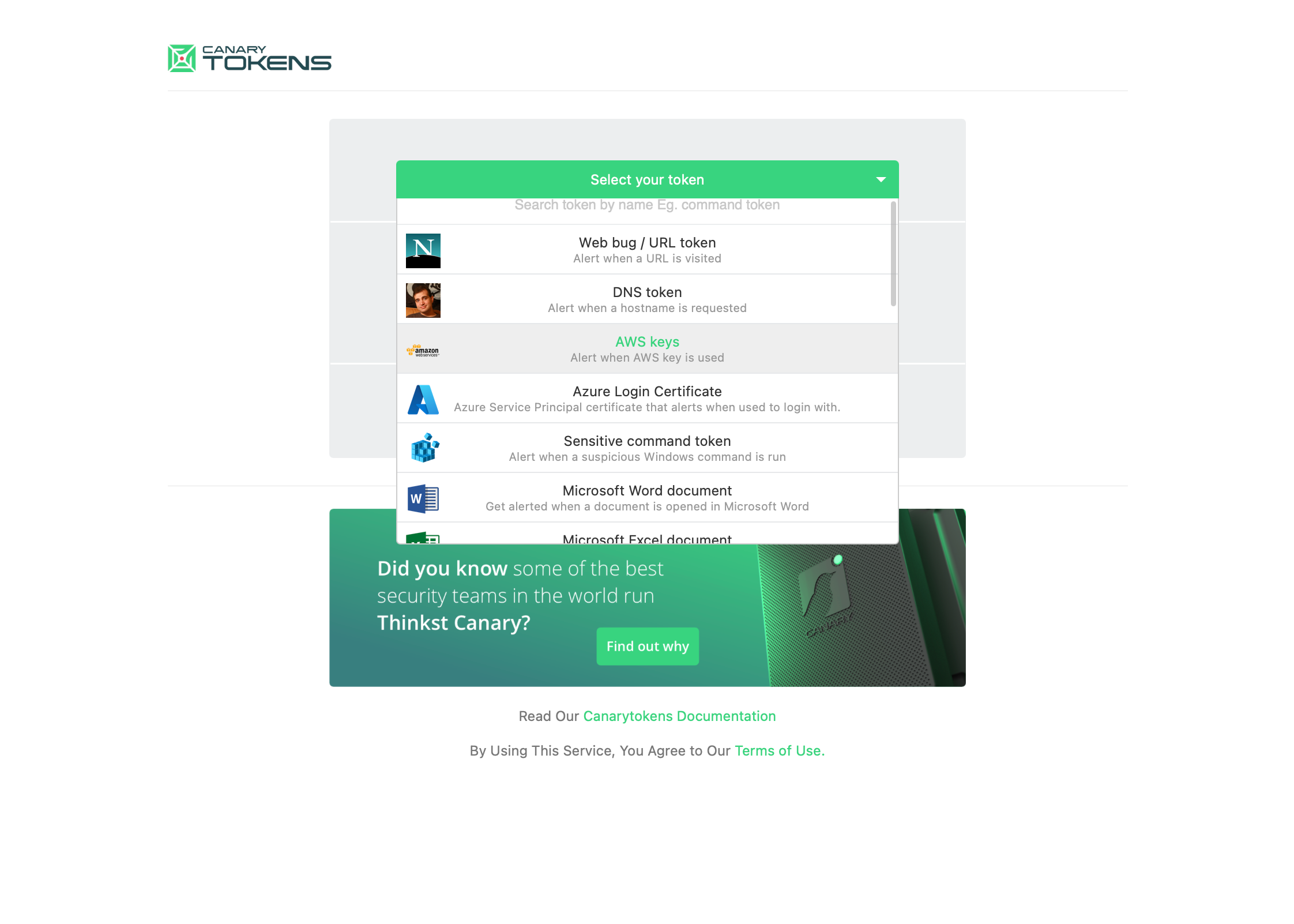
Canary Tokens
- Here we start, Ninjas!
I created an entire post about Canary Tokens a while ago, which you can see below. I was also about to write about IP Loggers but could not publish the article due to URL issues; before incurring any problems, I will not add any link, but you can get it from the picture or a simple Google Search. Remember to check what you click!
- Here are both links you chose…
FREE
NON-FREE
OK, what are Canary Tokens?
For those not confident within, Canary Tokens are files, webhooks, URLs or other formats that can gather information from who’s interacting within once created. For example, suppose you must collect a target location, but the target is on the alert about suspicious links. In that case, it may be easy to lead them to open a PDF file containing personal information rather than click a link. This is when Canary Token comes in handy and diversely from any previous App. This is easier to use and very user-friendly, free for personal use or a fee for business.
More info:
Here below are some pics that may help your searches



Here some more options….

I hope you now, understand the concepts of OSINT (Open-Source Intelligence) and offensive OSINT. By familiarising yourself with these concepts, you will have an extensive range of tools to handle online security threats. Online security threats continue to increase daily. Therefore, it’s essential to be proactive in safeguarding our digital assets. With your current knowledge, you can apply various techniques to protect your online privacy.
It doesn’t matter whether you are a student, researcher, professional, or just an ordinary person; it’s crucial to be mindful of privacy and use your newfound knowledge responsibly.
For instance, you can use OSINT techniques to find publicly available information about yourself and take steps to remove it if necessary.
However, it’s crucial to note that using OSINT or Hacking techniques for malicious purposes can lead to severe consequences. Engaging in illegal Hacking can result in legal action against you. Therefore, it’s essential to exercise caution and act within the boundaries of the law.
Remember, using your skills and knowledge for ethical purposes can positively impact society.
>>>As usual, Stay Tuned 4 More & Share 4 All! ->